Technology
SECURITY THREATS ALL ONLINE BUSINESSES SHOULD BE AWARE OF WITH THEIR SOLUTIONS

Just as security of one’s country requires round the clock protection from Imposters, online businesses also need to be vigilant of various security threats challenging them. The massive Internet boom has made life easier and faster for all. As online shopping becomes a more viable and convenient option for consumers, E-commerce companies need to address unique obstacles that stand in their way.
If one’s business has an online presence, one should be concerned with security in general. But for Companies who deal in monetary functions on a daily basis, then one should be pre-occupied and constantly worrying about the security threats and how to keep them at bay.
The most common threats e-commerce sites face are:
Spam
Blog comments and contact forms are an open invitation to spammers that want to leave infected links on our sites or waiting for you in the inbox. This not only effects the site security but site speed too.
“Mass mailed malware infection can quickly morph into a machine serious problem, “says
Brian Krebs, Data Security expert.
Phishing
Several e-commerce shops receive reports from their customers who have received messages or e-mails from hackers in disguise, it could be a masquerade attack where the attacker pretends to be an authorized user of a system in order to gain access or to gain greater privileges than authorized for. This may be attempted using stolen login ID’s and passwords through finding security gaps in the program or through bypassing the authentication mechanism. This method only works if one follows through the action and gives access to one’s login information or other personal information data.
Phishing attack example:
A spoofed email ostensibly from myuniversity.edu is mass-distributed to as many faculty members as possible.
The email claims that the user’s password is about to expire. Instructions are given to go to myuniversity.edu/renewal to renew their password within 24 hours.
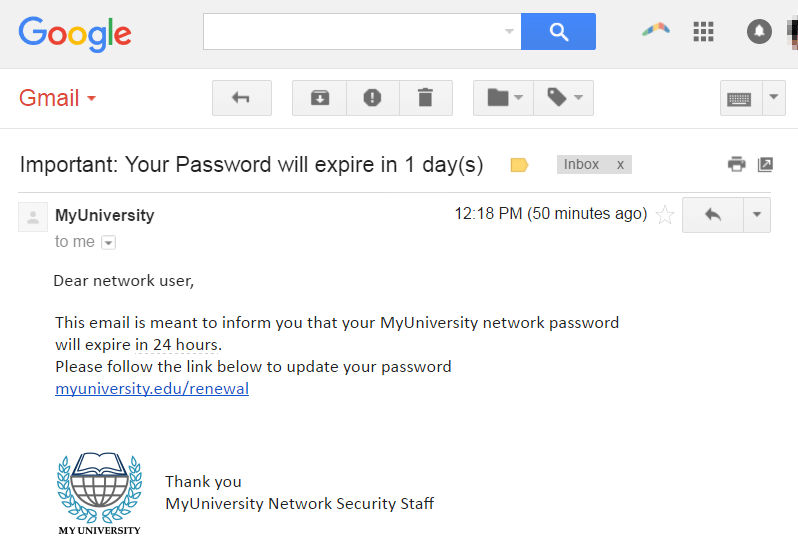
Several things can occur by clicking the link. For example:
The user is redirected to myuniversity.edurenewal.com; a bogus page appears asking for both new and existing passwords. The attacker, monitoring the page, hijacks the original password to gain access to secured areas on the university network.
The user is sent to the actual password renewal page. A malicious script activates in the background to hijack the user’s session cookie. This results in a XSS attack giving the hacker access to the university network.
Bots
Bots or internet robots are also known as spiders, crawlers, and web bots. While they may be utilized to perform repetitive jobs such as indexing a search engine, they often come in the form of malware. Malware bots are used to gain total control over a computer.
The Good
One of the typical Good bot uses is to gather information, automatic interaction with instant messaging, instant relay chat or assorted other web interfaces. Dynamic interaction with websites is yet another way bots are used for positive purposes.
The Bad
Malicious bots are defined as self-propagating malware that infects its host and connects back to a central server (s). The server functions as a ‘command and control centre’ for a botnet. These bots have “worm likeability to self propagate” and can also gather passwords, log keystrokes, obtain financial information, relay spam, capture and analyze packets, launch DoS attacks, open back doors to the infected computer and exploit back doors opened by viruses and worms. Bots are usually used to infect a large number of computers which form a” botnet” or bot network.
Some attackers develop special bots that can scrape one’s website to get information about inventory and prices. Such hackers, usually our competitors lower the prices in their websites to lower our sales and revenue.
Malware
Malware is a piece of software intentionally designed by cybercriminals to cause damage to a computer server. Inserted into web pages through techniques like SQL Injection, malware files can allow hackers to fake their identity, take control of computers and networks, tamper with the database, send malicious e-mails on our behalf and gain access to all the data on our system.

Distributed Denial of service (DDoS) Attacks
DDoS attacks target websites and online services. The aim is to overwhelm them with more traffic than the server or network can accommodate. The goal is to render the website /service inoperable. The DDoS attack depletes the server resources and increases the website load time. The security threats can cost our business thousands in lost revenue and mitigation. However, costliest damage done by DDoS attacks is often reputational –losing our customers ‘trust and confidence.
Financial Frauds –Credit Card frauds
This happens when a cybercriminal uses stolen credit card data to buy products on an e-commerce store. Usually, in such cases, shipping and billing addresses vary. One can detect and curb such activities in one’s store by installing an AVS –Address Verification System.
Another form of credit card fraud is when a fraudster steals personal details and identifies to enable them to get a credit card.
Exploitation of known Vulnerabilities
Attackers are hawking for certain vulnerabilities that might be existing in an e-commerce store. Often e-commerce stores are susceptible to SQL Injection, cross-site scripting (XSS).
SQL Injection is a malicious technique where a hacker attacks the query submission form to access our database. They corrupt the database with an infectious code, collect data and later wipe the trail.
XSS –The attackers can plant a spiteful JavaScript extract on e-commerce store to target online visitors and customers. Attackers inject malicious scripts into websites. Such culprits send a malicious code as a browser script to a different user. Such codes can access customer cookies and compute.
E- Commerce security solutions that can ease our lives are as follows:
Server Security
We should ensure that our site security is on top of the mind of the web hosting company. As the server interconnects computers, they are the hub of a lot of valuable information that can be accessed. Protection of these accessible information assets from a web server is known as Server Security. Web server security becomes highly important when it is connected to the internet. Protocols like SSL and TLS provide server and client authentication and encryption of communications.
Some easy steps to follow against the hackers –
Install only necessary software.
Close all the network ports.
Filter the openings you cannot block.
Hide all version information.
Check and update regularly
HTTPS and SSL certificate
HTTPS helps in securing data transfer between servers and the user’s devices. Thus preventing 3rd party interception you should buy an SSL certificate for your website that provides security for online communication. When a web browser contacts your secured website, SSL certificate enables an encrypted connection. It is kind of like sealing a letter in an envelope before sending it through the mail.
Payment Gateway Security
Avoid storing Credit card information of your clients on a database and let a third-party handle payment transaction away from the website.
Anti-virus and anti-malware software
An anti-malware is a software program that detects, removes and prevents infectious software from infecting the computer and IT systems. Since malware is an umbrella term for all kinds of infections including worms, viruses, Trojans etc, getting an efficient anti-malware would do the trick. Serving our PC and other complementary systems with an anti-virus keeps a check on all infections.
Firewall
Effective firewall keeps away fishy networks, XSS, SQL injections and other cyber attacks. They also help in regulating traffic to and from the online store, to ensure the passage of only trusted traffic.
Employ multi -layer security
We can improve our security by using various layers of security. We can use a widespread Content Delivery Network (CDN) to protect from DDoS attacks and malevolent incoming traffic. Two -factor authentication can be squeezed in as an additional layer of security.
E-commerce security plugins
These are simple ways to enforce security protection against bad bots, SQLite, XSS, code injections and other severe attacks.
To sum up, besides keeping back-up of data, staying updated, training our staff better and even educating our clients /customers, we also need to do regular site security audits to stay ahead of the dangers. There is no room for mistakes as one critical failure will cost our business. Therefore the best approach is to invest in e-commerce security as much as we invest in its marketing and Webdesign. This would be money well spent as there is nothing better than winning faith and confidence of our clients and having a secure environment for business.If the pillars of business are strong then our business is here to stay!!